Selected Projects.
 |
|
StorageFabric
High Performance Software-Defined Storage Unification and Protection Fabric
|
|
 |
|
ENFORCER SRX1
World's first general-purpose FIPS 140-2 Level 4 Secure Server
Sponsors: NSF, Air Force, IARPA, DHS, Navy/ONR, others
|
|

|
|
DECAF
Automatic, Adaptive De-bloating and Hardening of COTS Firmware
Sponsors: ONR
Research:
2020usenixsec.2
|
|

|
|
REARM
Protecting ARM Binaries via Load-time Reduction and Run-time Read-Protection
Sponsors: ONR
Research:
2020usenixsec
|
|
 |
|
CipherLocker
Zero Trust Drag and Drop File Sharing Platform
Sponsors: NSF, others
|
|

|
|
Plausible Deniability
Practical Plausibly Deniable Encryption through Low-Level Storage Device Behavior.
Sponsors: NSF CNS SatC 1526707
Research:
2015tifs,
2016oram-ccs,
2016datalair-ccs,
2017apsys,
2017pets,
2019pets,
2019ndss.2,
2020pets,
2020pets.2,
2021usenixsec
|
|
|
|
Sensorprint
Hardware-Enforced Information Authentication for Mobile Systems.
Sponsors: NSF CNS CSR 1526102
|
|

|
|
Smart Grid Android Manager.
Android-Based Smartgrid Management.
Sponsors: DOE
|
|
 |
|
National Security Institute
The National Security Institute (NSI) vision and core mission is to secure our homeland by researching and developing technologies and insights for secure, trustworthy, and available communications and computing platforms.
We're hiring!
|
|

|
|
uID: A Strongly-Secure Usable Identity Ecosystem with Privacy.
A secure, usable, privacy-enabling digital identity ecosystem able to integrate, and synergize
with existing governmental, commercial and open-source identity and authentication solutions.
Research:
2012.uid.vision,
2012.uid.proposal
|
|
 |
|
Cloudtracker.
Transparent, Secure Provenance Tracking and Security Policy Enforcement in Clouds.
Sponsors: NSF CNS 1161541
Research:
2014cloudflow,
2014sok
|
|

|
|
Green Hadoop.
Cost and Energy-Aware Cloud and HPC Computing.
Sponsors: NSF CNS 1318572
Research:
2013lips-hipc,
2014socc,
2015ccgrid,
2017tcc-affordhadoop
|
|
 |
|
NFS4Sec.
An Extensible Security Layer for Network Storage
Sponsors: NSF CNS 1223239
|
|

|
|
Security and Privacy in Geo-Social Networks.
Sponsors: US ARMY
Research:
2011gis,
2012geosocial
|
|
 |
|
Secure Provenance in High-End Computing Systems.
Designing secure provenance mechanisms for high Performance Computing.
Sponsors: NSF CCF 0937833
Research:
2007storagess-provenance,
2009sprov-fast,
2009remembrance-cidr,
2009sprov-usenix-login,
2009sprov-tos,
2010tapp,
2011worm-tifs,
2011socc-ccost
|
|

|
|
Optimal cloud-scale resource co-scheduling of data and computation.
Sponsors: TBA
Research:
2011hpdc-xen
|
|
 |
|
CAREER: Practical Privacy for Outsourcing Systems.
Mechanisms for secure data outsourcing, private information retrieval and oblivious transaction processing.
Sponsors: NSF CAREER CNS 0845192
Research:
2006pir-panel,
2007pir,
2007sdo-chapter,
2007ns2demo,
2007sdo-tutorial,
2008pir-ndss,
2008pir-ccs,
sion2009otp-ndss,
sion2009ccsw,
sion2009mitTR3,
sion2009mitTR2,
sion2009mitTR,
2010worm-oram,
2010private-join,
2010fc,
2010fc-workshops,
2010wpes-pcost,
sion2010mitTR4,
2010cloud-cpu,
2010cloud-rds,
2010cloud-storage,
2010cloud-http,
2011cloud-cpu2,
2011pir-tissec,
2011cloud-net1,
2011fc-oram,
2011cloud-net2,
2011cloud-elb,
2011private-join,
2011cloud-sqs,
2011socc-ccost,
2012sroram,
2012privatefs-ccs,
2012pir-ccs,
2013deb-pcost,
2013oram-tissec,
sion2015atc-concurdb
|
|
 |
|
cDB: Strong Regulatory Compliant Databases.
Regulatory compliance for relational databases
Sponsors: NSF IIS 0803197,
CRI CNS 0708025
Research:
2007sdm-health,
2007storagess-provenance,
2009sprov-fast,
2009remembrance-cidr,
2009sprov-usenix-login,
2009sprov-tos,
2009compliance-chapter,
2011sigmod-trusteddb,
2011worm-tifs,
2011worm-oram,
2011private-join,
2011vldb-trusteddb-demo,
2013tkde-trusteddb,
2013vldb-correctdb,
2013ficklebase-icde,
2013hifs-ccs
|
|
 |
|
The Stony Brook Trusted Hardware Lab.
The THL (established in the Fall of 2007 as part of the NSAC Lab)
constitutes a central academic expertise and research knowledge repository
on secure hardware, a nation-wide first of its kind. It will support
community-wide educational and research activities, and provide direct hands-on
or networked access to remote or visiting research community members. Plan to
visit ? Do not hesitate to contact us.
Sponsors: NSF CRI
CNS 0708025, IBM Cryptography Software Group
Research:
2008hardware-tutorial-usenix,
2008hardware-tutorial-ccs,
2009hardware-tutorial-oakland,
2010pufs
|
|


|
|
Secure Sensing.
|
|
 |
|
NS3: Networked Secure Searchable Storage with Privacy and Correctness.
Robust, efficient, and scalable content-search mechanisms for networked data
storage with confidentiality, search pattern privacy, and data retrieval
correctness.
Sponsors: NSF CNS 0627554,
CRI CNS 0708025
Research:
2006pir-panel,
2007pir,
2007sdo-chapter,
2007ns2demo,
2007sdo-tutorial,
2008pir-ndss,
2008pir-ccs,
2009otp-ndss
|
|
 |
|
Miscelaneous Applied Crypto/Security.
Having fun with Dick and Jane.
Sponsors: NSF
Research:
2006rep-fc,
2009wpes-xpay,
2010cec,
2012tifs-xpay
|
|
 |
|
Secure Document Management.
Infrastructure for document management with secure provenance assurances.
Sponsors:
Xerox
Research:
2007storagess-provenance,
2009sprov-fast,
2009remembrance,
2009sprov-usenix-login
|
|
 |
|
SecureWORM: Strong Regulatory Compliant Storage.
A regulatory compliant store with guaranteed data
retention and deletion, quick lookup, and compliant migration.
Sponsors: NSF CNS 0716608,
CRI CNS 0708025
Research:
2010worm-oram,
2008worm-icdcs,
2007worm-chapter,
2007worm-tutorial,
2007sdm-health,
2007storagess-provenance,
2007eds-WORM
|
|
 |
|
Personal DRM in cellular contexts.
User-level DRM controls for content access, data integrity and rights management in cellular contexts, enabling
enforcement of ORCON-type policies.
Sponsors: Motorola Labs
Research:
2007drmdemo,
2009drm
|
|
 |
|
Secure Location Certification for Sensor Networks.
Achieving Assurances for Location Claims for Sensor Network
Data Flows in Hostile Environments.
Collaborators: Jie Gao, Sol Lederer
Sponsors: CEWIT
Research:
2009sensors,
2008sensors,
2007sensors
|
|
 |
|
SQi: The Secure Query Interface.
A secure extension to a legacy query interface to allow for proofs of query execution,
correctness and completeness. It is extensible in that it allows for arbitrary plugins
to be written for additional expression ability (e.g. a constraint plugin that could
be used to handle privacy constraints and enforce inference controls). It allows for
access to any arbitrary (set of) remote data sources.
Research:
2005sdo-vldb
|
|
 |
|
IBM Almaden (2004)
In the On Demand and Grid Computing Group,
at the IBM Almaden Research Lab I
was responsible for designing and implementing a data-aware grid scheduling infrastructure.
Research:
2004xg-icdm,
2005xg-jsspp,
2005xg-dexa,
sion2006xg-edbt
|
|
 |
|
Rights Assessment for Discrete Digital Data.
A foundational framework for Digital Rights Protection through
Information Hiding, an important part of my doctoral dissertation.
Research: 2002:NLW,
2002nrwm,
2002wmpower,
talks,
ONR Proposal,
CERIAS Proposal,
Proposal NSF,
CERIAS TR 2002-30,
CERIAS TR 2001-54,
2002wmdb-sigmod,
2002wmbounds,
2002wmss,
2003categorical,
2003wmdb-icde-demo,
2003wmsensor-VLDB,
2004thesis,
sion2006wmdb-tutorial
|
|
 |
|
NEC Internship (Summer 2003)
My work at NEC Research in Cupertino. I work on
security and monitoring for Web Service Business Workflows.
Research: 2005wsmon-icws
|
|
 |
|
WMDB: Relational Database Watermarking.
A new theory and proof-of-concept software implementation
for watermarking and information hiding in a relational data
framework. It includes a user-friendly GUI and enables remote
access to any arbitrary SQL database.
Research: 2002nrwm,
2002wmpower,
CERIAS TR 2002-28,
2002wmdb-sigmod,
sion2003categorical,
sion2003wmdb-icde-demo,
2005wmdb-chapter,
2007wmdb-chapter
|
|
 |
|
MATRIX. Peer to Peer CPU Sharing.
Matrix aims at using Peer to Peer computing in sharing CPU cycles.
|
|
 |
|
NEC Internship (Summer 2001, Spring 2002)
My work at NEC Research in San Jose. I worked on building
a cache for dynamic database web driven sites as well as
in the area of content based delivery networks.
Research: 2002vldb,
TR at NEC Research 2001,
TR at NEC Research 2002
|
|
 |
|
XPRO: IP Router
A quite nice project, resulting in the writing from scratch of a TCP/IP Router,
including NAT, firewalling, network snooping, remote logging etc. I worked in a
team of 4 on this and wrote most of the routing structures, RIP, firewalling, control
interface, others. I invented a new routing structure, the TRIX. Was lots of fun.
Under the supervision of Doug Comer,
the ultimate authority on this matter.
Research: report
|
|
 |
|
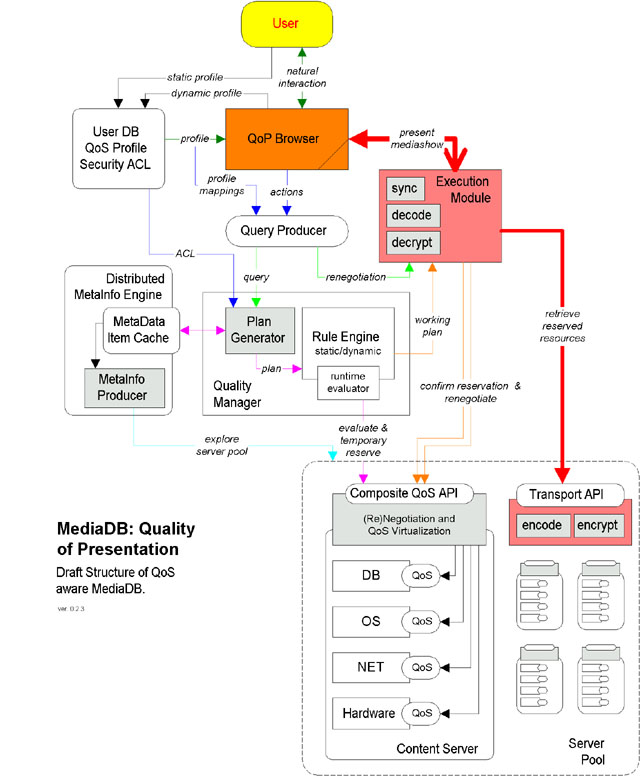
QUASAR: Quality of Service Aware Repository
During my PhD, I briefly worked on QoS for high performance databases.
Research: TR at Computer Sciences,
2003quasaq-edbt
|
|
 |
|
IBM Internship (Summer 2000)
My work at IBM Transarc. This was my first internship
in the US. I worked in an R&D environment where
i developed an "object browser" for WebSphere tm.
as well as some other applications including
a stock quote retrieval application using EJBs,
hot technology at the time.
|
|
 |
|
The MicroServer
During my brief involvement with the Bond Agent System,
together with L. Boloni, I came up with an
idea of enabling access to methods and object through a HTTP interface (long before SOAP came about !!!).
This resulted in the MicroServer concept and implementation. It did not get finalized due to
largely political reasons. We nevertheless got a paper out of it.
Research: micros2000
|
|
 |
|
The Bond Agent System
In the first days of my PhD, I was co-opted to work in the
Bond Agent System
Research lab (moved to Florida now). I changed my research topic after my first year but
nevertheless wrote some agents code and parts of a Bond beginners manual. This resulted also in
a peer-reviewed paper and several tech-reports.
Research: 2000asama,
TR-CS-BOND-2000,
TR-CS-ACL-2000
|
|
 |
|
Talking Objects.
A distributed servicing system on top of JVM done during
my undergraduate college years (1996-98). The main idea was to use
natural language in inter-entity communication and service
advertisments. Maybe I will
continue this sometime in the future.
Research:
TR-CS-PUB-talking-nl-1999,
TR-CS-PUB-talking-id-1999,
TR-CS-PUB-talking-1999
|
|
 |
|
JVM: The Jet (Java) Virtual Medium
This is my main undergraduate thesis.
JVM is designed to use some of the advanced (in late 1995:))
features of java in order to create a friendly interface to a virtual
networked community. It is basically a distributed system enabling
a set of clients to transparently communicate by exchanging arbitrary
objects through itself.
Research:
TR-CS-PUB-distrib-1999
|
|